The trend of IT and OT merger
Asia - Pacific (APAC) is considered the leading region in the wave of digital transformation globally. Industrial sectors in the region are rapidly applying automation, real-time data and connecting infrastructure, making the integration of information technology (IT) systems and operating technology (OT) an essential factor to improve efficiency and business efficiency.
However, this combination also leads to many new cybersecurity vulnerabilities. As the boundary between the two systems becomes increasingly blurred, the vulnerable area is expanding, posing more challenges for organizations in the region.
The latest data from Kaspersky's Industrial Control System Response Center (ICS-CERT) shows that key sub-regions in the Asia-Pacific region are still experiencing a wave of cyber attacks targeting ICS computers (industrial control systems), said Adrian Hia, Executive Director of Asia - Pacific (APAC).
In the first quarter of 2025, Southeast Asia ranked second globally, Central Asia ranked third and South Asia ranked sixth in the rate of harmful subjects in ICS computers.
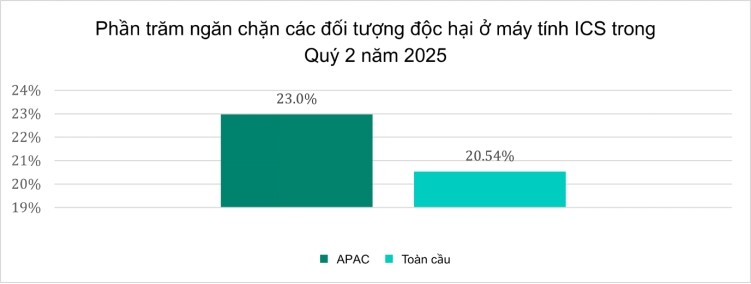
In the second quarter of 2025, industries most affected by viral threats in the Asia-Pacific region include: electricity, building automation, oil and gas, manufacturing, engineering and ICS system integration.
Also from April to June 2025, countries affected by the ICS computer attack virus include Vietnam, Afghanistan, China, Bangladesh, Pakistan, Myanmar, Laos, Cambodia, Indonesia and Nepal.
The core role of a Smart Security Operating Center (SOC)
Faced with growing threats to critical infrastructure in the Asia-Pacific (APAC) region, Kaspersky cybersecurity experts recommend that businesses adopt a multi-layered cybersecurity framework. The core of this framework is a smarter Security Operations Center (SOC).
According to Mr. Hia, the center will start with a prevention layer, using threat intelligence tools such as brand protection, attack Sources and Invasion Cards (IoC) to detect dangers early before they can attack.
The second layer focuses on protection, with advanced tools such as Endpoint leaders like Endpoint leaders like Endpoint leaders like detect and respond (EDR), Management drivers like MDR, and Expanded leaders like detect and respond (XDR).
To help businesses protect themselves from many types of threats, Kaspersky experts offer some recommendations:
- Conduct periodic security assessments of OT systems to detect and promptly fix security vulnerabilities.
- Apply security patches or remedies for key components in the OT network as soon as possible, helping to prevent serious incidents that could cause major damage due to production disruptions.
- Building and strengthening incident prevention, detection and response skills for cybersecurity teams is the core to deal with new attack techniques.
Intensive OT security training courses for both IT security and OT personnel play a key role in this.
- Use in-depth security solutions to check security, detect and respond to threats and incidents across the entire distributed infrastructure.
- Building a unified Security Operations Center (SOC) capable of comprehensively monitoring both the IT and OT systems is necessary.











