Wrong password and perfect phishing scheme
In June 2023, the CyProtek investigation team of the Anti-Fraud project received a series of complaints from users about bank accounts being suddenly locked for no apparent reason. The victims all told a similar story: After their accounts were locked, they received a call from a "bank employee" asking for an OTP code to recover them. Just a few minutes later, the assets in the account "evaporated".
Initial analysis suggests that these are not isolated incidents, but rather part of a larger fraud campaign targeting banks in Vietnam. The CyProtek team decided to get involved, assigning the investigation code 23xPH03NIX, part of an international cyberattack campaign called GoldFactory.
"Account Lock" Tricks - The Starting Point of a Scam
According to the investigation, hackers start by collecting victims' information from leaked data sources or online black markets, including phone numbers, emails, login names, and even passwords. Notably, many of the data are accidentally revealed by the victims themselves through social networks or unsecured online platforms.
Once they have enough information, the hacker logs into the victim’s bank account. They intentionally enter incorrect information multiple times to lock the account. This is the perfect “knot” to start the scam scenario.
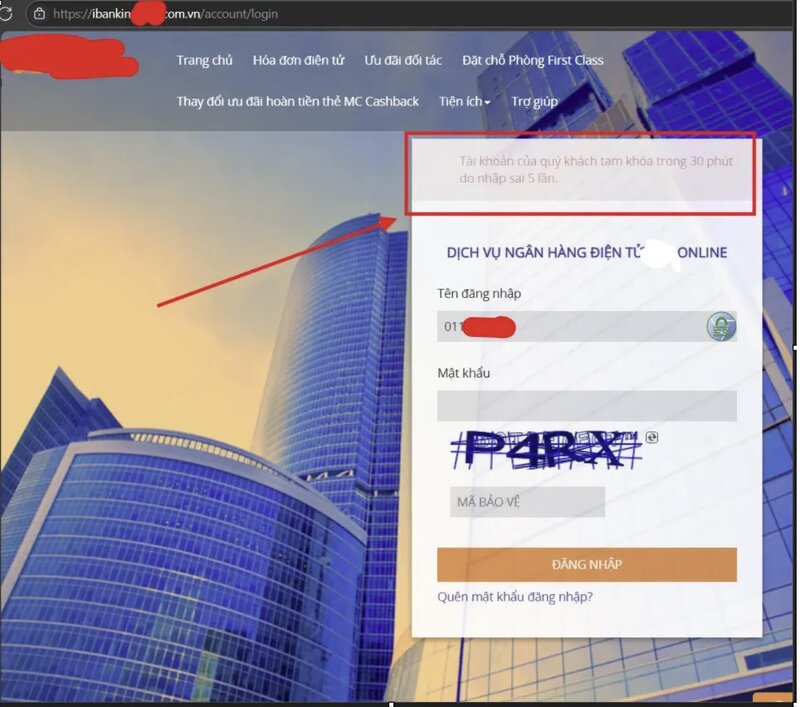
Fake bank employee call
When an account is locked, the victim receives a call from someone claiming to be a bank employee. This person informs that the account has been locked due to suspected unusual activity. They quickly provide accurate information about the victim's account - from account number to recent transactions - to build trust.
The hacker then asks the victim to provide an OTP code to “verify and reopen the account” through a fake website in order to hijack the bank account. In a state of panic, most victims do not suspect anything and follow. But when the OTP code is sent, the hacker immediately makes money transfers or steals assets.
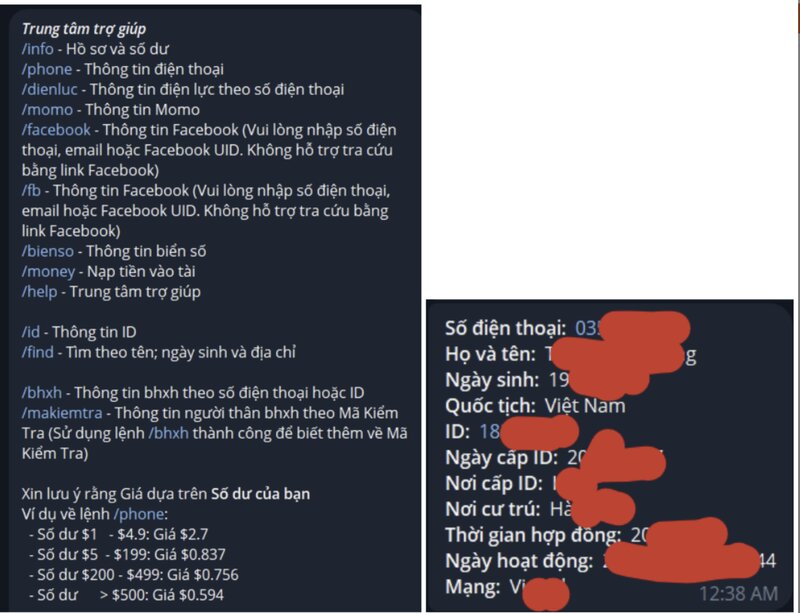
The hacker's well-organized system of operations
CyProtek’s analysis shows that the hackers in the GoldFactory campaign did not operate alone, but in a systematic manner. They would perform several steps:
Buying personal data: From black markets that trade data, including leaked data from large corporations.
Understand banking security procedures: Exploit loopholes in locked account handling mechanisms.
High-tech: Using tracking software and fake apps to optimize attacks.
Over the past two years, the hacker group has created more than 421 fake websites to spread malware and deceive victims. This network not only operates in Vietnam but also has links with cybercrime groups in Cambodia, Myanmar and China.
Identify and protect yourself from new tricks
The CyProtek investigation team of the project emphasized that users need to be aware of the following signs to protect themselves:
Never provide OTP code over the phone: Banks do not ask for this information in any form.
Beware of calls from unknown numbers: Check information through the bank's official switchboard before taking any action.
Check transaction history regularly: Detect suspicious transactions promptly.
The investigation team's journey has exposed an organized cybercrime network with sophisticated and large-scale tricks. These findings are not only a wake-up call for users, but also pose a challenge for banks to improve their security systems.
As hackers become more and more professional, users' vigilance and understanding will be the most important shield. "One minute of carelessness, a lifetime of paying the price" - always be careful when using online banking services.









