Continuing the series on the GoldFactory campaign, the CyProtek investigation team of the Anti-Fraud project continues to reveal another sophisticated trick - using fake applications to appropriate assets.
When your phone becomes "delicious bait"
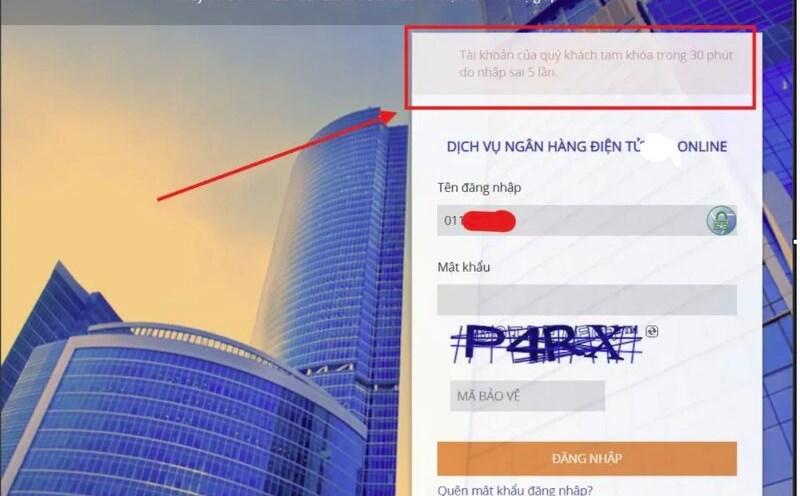
CyProtek’s investigation not only exposed the “account lockout” tactic, but also revealed how the hackers used fake apps to take full control of the victim’s device. This is an upgrade in the GoldFactory cyberattack campaign, making the scam more dangerous and difficult to detect.
These apps are often distributed through fake websites. During the 277-day investigation, the investigation team discovered more than 421 websites designed to lure victims into installing malware.
The Journey of a Fake App
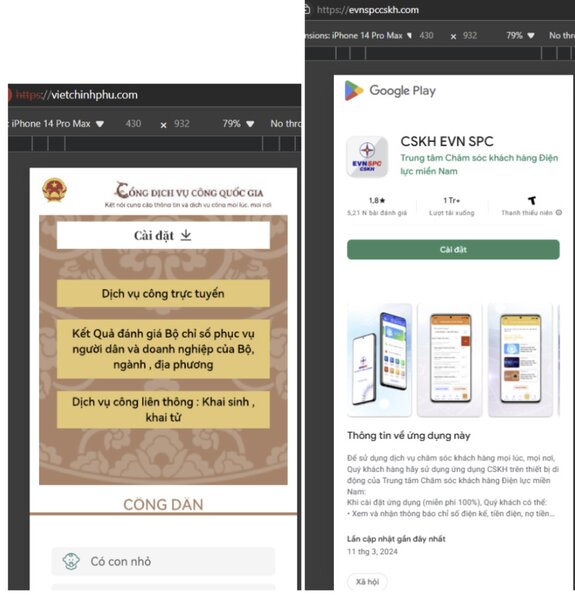
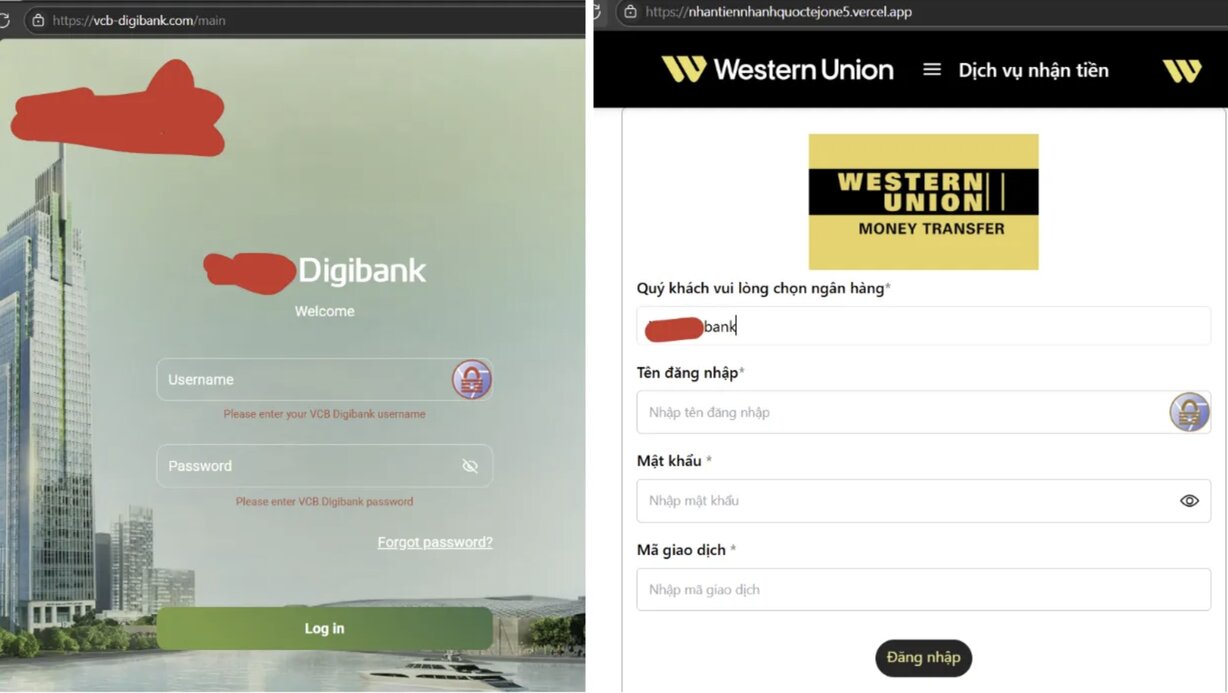
These applications are not simply "strange" software. They are elaborately designed with eye-catching interfaces, names similar to banking applications or reputable organizations such as Public Security (VNEID), Social Insurance (VSSID), Electricity (EVN), Tax Department (ETax Mobile) or online public services. Hackers often approach victims via SMS, Zalo, or fake calls, asking them to download the application via the attached link.
“When the victim clicks on the link, the .apk file (for Android) or other fake software will be downloaded to the phone. Once installed, the app will ask for deep access permissions such as accessibility, message reading, and file access. This is when the hacker takes control of the device,” the investigation team analyzed.

Accessibility permissions - "back door" for hackers
Once accessibility permissions are granted, the rogue app can:
Track all device actions: Including password and OTP code entries.
Deletion or alteration of data: Messages containing OTP codes or notifications from banks can be deleted before the victim can read them.
Overlay: Display a fake screen to trick the victim into thinking the transaction is being done securely with their biometric face.
“There are cases where victims have provided OTP codes to hackers without knowing it, because they believed they were working with the bank's official interface,” the CyProtek team shared.
Signs that your phone is being controlled
The CyProtek team has compiled common signs when a phone has a fake application installed:
The machine runs slow and gets hot abnormally, even when not used much.
Battery drains fast, mobile data traffic spikes.
Strange applications appear that the user does not remember installing.
Messages, notifications from banks or apps are deleted automatically.
Some settings on the phone are changed, like enabling unknown access or accessibility permissions.
Startling numbers from the investigation
The investigation team analyzed data from more than 64 servers used by hackers to control victim devices, and discovered that hundreds of accounts were taken over within hours of the fake app being installed.
"Hackers not only make money transfers but also exploit personal data such as photos, videos, and sensitive information to carry out other fraudulent acts," said Mr. Ngo Minh Hieu, a representative of the group.
How to avoid falling into the fake app trap?
Based on the investigation results, the CyProtek team recommends users to:
Only download apps from official sources: Google Play Store, Apple App Store.
Don't click on links from unknown sources: Messages or emails with strange links attached are suspicious signs.
Check app access: Do not grant accessibility or device administration permissions to apps from unknown sources.
Use antivirus software and firewalls: Make sure applications are installed securely.
Beware of .apk file download requests: This is a common way to distribute malware on Android.
Fake apps are not only a tool for hackers but also a lesson for all users. In the digital age, protecting personal devices is not only a responsibility but also the only way to protect your assets and identity.
Remember: no reputable bank or organization will ask you to download apps from unofficial sources. Your vigilance is the best defense against hackers' sophisticated tricks.