Recently, all Chrome browser users around the world have once again faced alarming security risks. A serious vulnerability was discovered with identification code CVE-2025-5419, belonging to the out-of-bounds read/write group in the JavaScript V8 processing tool, an important component of this browser.
Worryingly, Google has officially confirmed that this vulnerability is being exploited in practice, which means that cyber attacks have been taking place and are no longer at the potential level. "We have known of extra Natural exploitation for CVE-2025-5419," said a Google representative.
To ensure and minimize risks while users are unable to update, Google has quietly implemented configuring changes from May 28, 2025 on all platforms. However, this is only a temporary solution.

Accordingly, this temporary configuration will not be able to replace the official "patch". For security reasons, Google will continue to limit technical details of this vulnerability until most users successfully update, or until affected third-party libraries are completely fixed.
It is known that CVE-2025-5419 is currently classified as a high-serious error, but the actual level of danger may exceed this level because it is being exploited directly.
According to a warning from the National Institute of Standards and Technology (NIST), this vulnerability could allow hackers to remotely execute malware through a manual code code page, a popular and highly difficult-to-detect attack method.
Not only Google, other browsers using chromium open source code such as Microsoft Edge, Opera or Brave will also be affected.
The impact of this vulnerability is so great that the US government has required all federal employees to update the Chrome browser, or stop using this browser until the update is complete. This is a common move in cases of national cybersecurity risks.
At the same time, the US Cyber Security and Infrastructure Agency (CISA) is also expected to include this vulnerability in the list of mandatory update requests within the next 21 days.
This emergency update also includes a second "patch" for the CVE-2025-5068 error related to Blink, Chrome's content display tool. This error was discovered by an independent security expert and reported to Google.
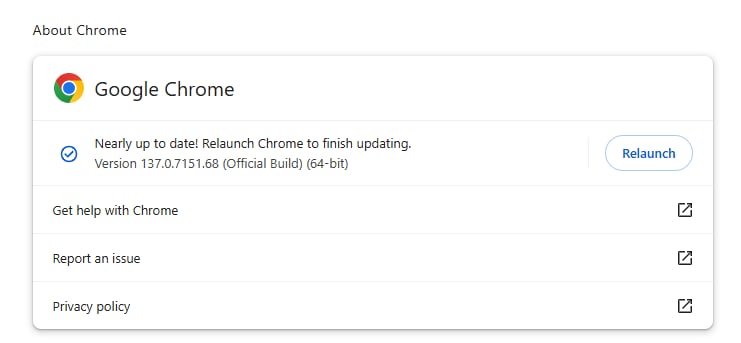
The new security update has now been released to Windows, macOS, and Linux. Users will see a warning icon or an Updated button on the right corner of the browser when the new version is ready.
You can also update manually by going to Settings - About Chrome, waiting for the browser to check, and automatically downloading the patch. Then press Relaunch to restart Chrome and apply the update.











